Writeup K3rn3l4rmy CTF: WiRE
by RetroFor this CTF we are provided with 2 files: an executable called WiRE-client.exe and a file containing some collected packets called WiRE.pcapng.
While opening the executable we cannot have any immediate clue about what is its purpose, we surely know that it is possible to open the pcapng file with a software like Wireshark.
It is sufficient to follow the TCP stream to see a strange message take shape:
..5"bt.vxgt.|t.w}pv.w~c.z.c..}rew.|h.utpc.btcgtc....4..Jb.rc.eni.cnctb.}g.unv..un{.s.L
that is clearly a crypted string. It is now that we begin to analyze the Client we’re provided with.

As we can see it requires a connection on port 9905… nothing that a netcat couldn’t solve! Let’s start it and we’ll see it i a communication client server, where a kind of cryptography is applied to the messages:

So let’s try to send the string we found before to the server:
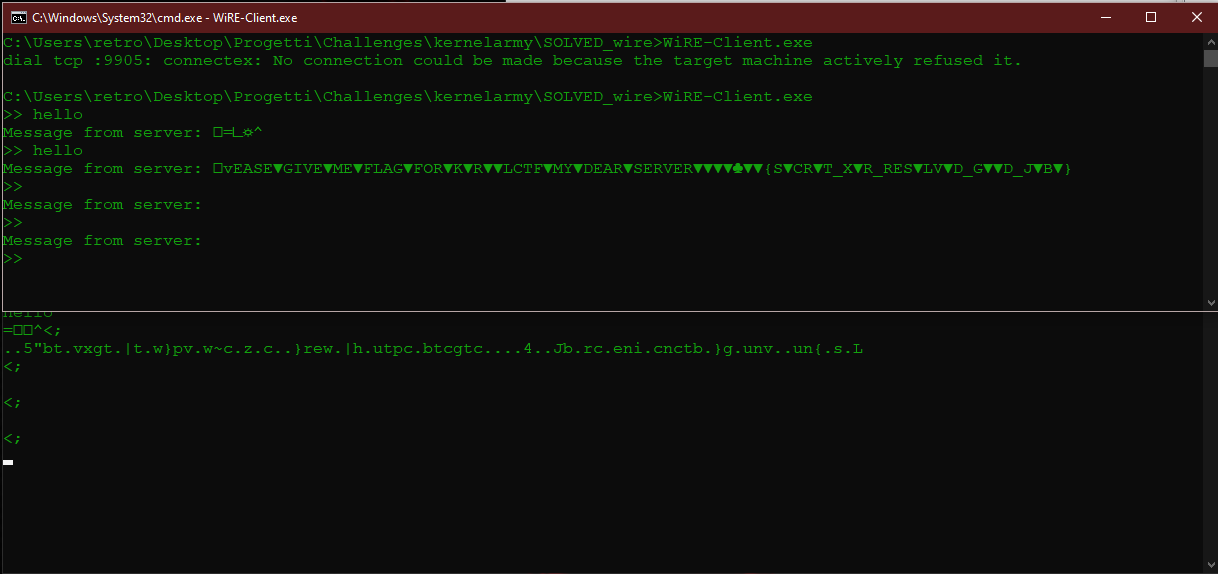
We can see familiar characters: we can infer something like:
PLEASE GIVE ME FLAG FOR K3RN3LCTF MY DEAR SERVER
and right after this some characters between curly brackets; we can see that the E and the O are correctly interpreted by the client, so the missing characters must be 3 and 0. In the end adding a ! at the end like most of the flags we get the answer:
S3CR3T_X0R_RES0LV3D_G00D_J0B!
The flag is in the format flag{…} so the flag we get is:
flag{S3CR3T_X0R_RES0LV3D_G00D_J0B!}
If you have any question, want to ask me anything or give me any advice, just contact me and I will be super-available to answer to all of you! Hope to see you again!
tags: Hacking - ReverseEngineering